Use your own TLS certificates
Estimated reading time: 2 minutesThis topic applies to Docker Enterprise.
The Docker Enterprise platform business, including products, customers, and employees, has been acquired by Mirantis, inc., effective 13-November-2019. For more information on the acquisition and how it may affect you and your business, refer to the Docker Enterprise Customer FAQ.
Docker Trusted Registry (DTR) services are exposed using HTTPS by default. This ensures encrypted communications between clients and your trusted registry. If you do not pass a PEM-encoded TLS certificate during installation, DTR will generate a self-signed certificate. This leads to an insecure site warning when accessing DTR through a browser. Additionally, DTR includes an HSTS (HTTP Strict-Transport-Security) header in all API responses which can further lead to your browser refusing to load DTR’s web interface.
You can configure DTR to use your own TLS certificates, so that it is automatically trusted by your users’ browser and client tools. As of v2.7, you can also enable user authentication via client certificates provided by your organization’s public key infrastructure (PKI).
Replace the server certificates
You can upload your own TLS certificates and keys using the web interface, or pass them as CLI options when installing or reconfiguring your DTR instance.
Web interface
Navigate to https://<dtr-url> and log in with your credentials. Select System from the left navigation pane, and scroll down to Domain & Proxies.
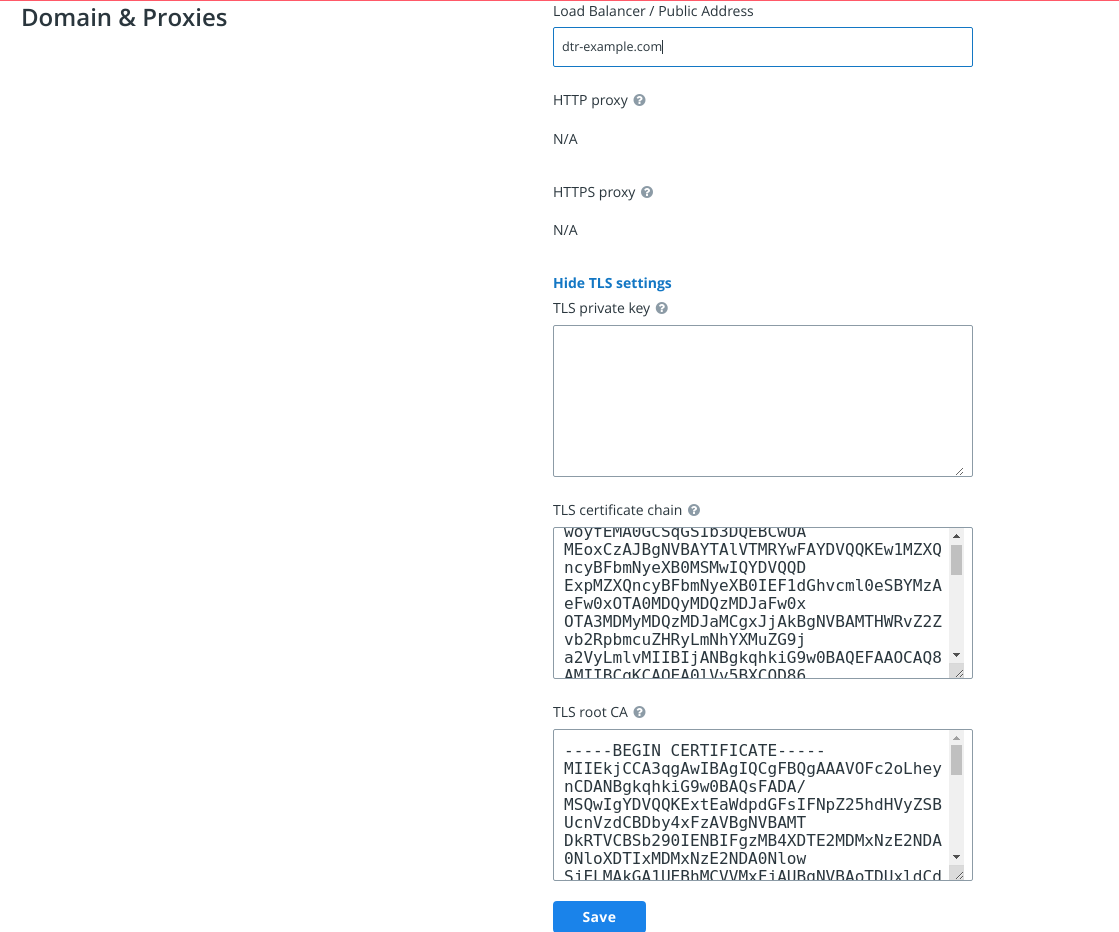
Enter your DTR domain name and upload or copy and paste the certificate details:
- Load balancer/public address. The domain name clients will use to access DTR.
- TLS private key. The server private key.
- TLS certificate chain. The server certificate and any intermediate public certificates from your certificate authority (CA). This certificate needs to be valid for the DTR public address, and have SANs for all addresses used to reach the DTR replicas, including load balancers.
- TLS CA. The root CA public certificate.
Click Save to apply your changes.
If you’ve added certificates issued by a globally trusted CA, any web browser or client tool should now trust DTR. If you’re using an internal CA, you will need to configure the client systems to trust that CA.
Command line interface
See docker/dtr install and docker/dtr reconfigure for TLS certificate options and usage.